Exposing services with Cloudflare Tunnel
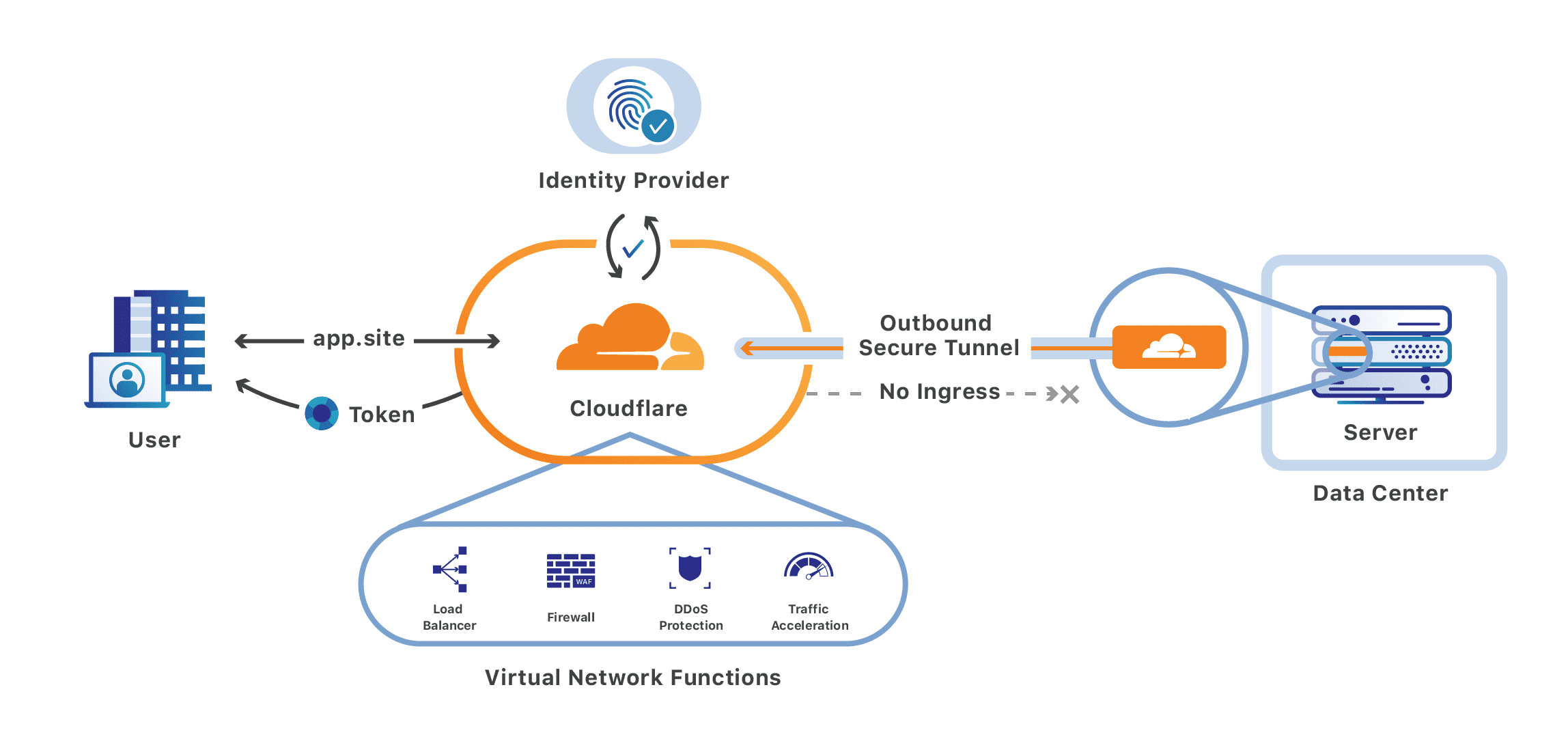
I have been wanting to setup an avenue for exposing select homelab services externally without opening holes in my firewall. In comesCloudflare Tunnels (formerly Argo Tunnels). I have used Cloudflare tunnels for several years at a former employer. It is a very cool piece of tech. Instead of routing traffic to an external IP address that has holes poked in a firewall, a service is run internally in your network. This lightweight service, Cloudflare Daemon (cloudflared) establishes an outbound-only encrypted connection to Cloudflare’s global network. The cloudflare tunnel is a persistent object that routes traffic to DNS records through Cloudflare’s proxy system. You can run many services through one tunnel. You can also remotely manage the tunnels now (this is a fairly new feature). Cloudflare tunnel is also now free for small deployments, which is perfect for a homelab setup.
Setup Cloudflared service internally
I have been using LXC Containers on proxmox to run several simple services using tteck’s Proxmox Helper-scripts. This has removed a bit of overhead for services I just need to work without much maintenance. Stay tuned for a future post to learn more about LXC Containers. To run cloudflared was very simple.
- Login to a proxmox node and grab the console
- Run the cloudflared install script from Proxmox scripts
1
bash -c "$(wget -qLO - https://github.com/tteck/Proxmox/raw/main/ct/cloudflared.sh)"
- Enable SSH so it can be used later by using the advanced setup or use proxmox console
Setup Cloudflare Tunnel
- Login to Cloudflare Dashboard and navigate to the Zero Trust area. Go to Networks → Tunnels
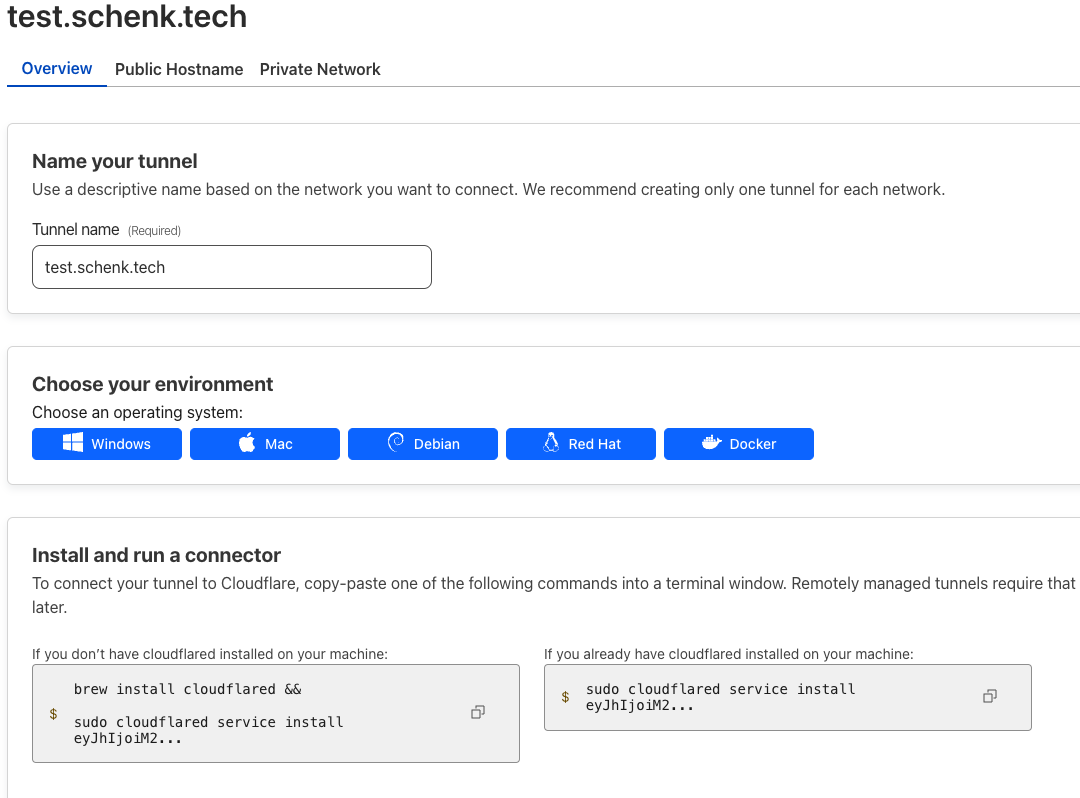
- Create a new Cloudflared tunnel, name the tunnel. like
test.schenk.tech. Click Save Tunnel - Note the cloudflared command to run
- SSH to cloudflared service
-
Run service install command from cloudflare dashboard. Click Next
1
sudo cloudflared service install SOME-SECRET-TOKEN-STRING
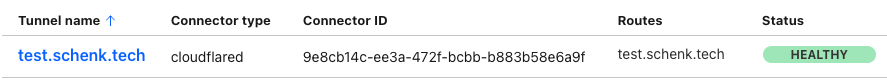
Once the outbound connection is established with the Cloudflare global network, you will see a healthy connection
-
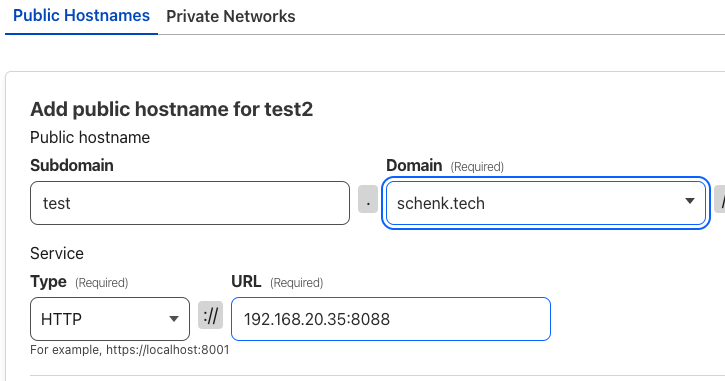
Setup a public hostname ,
test.schenk.techis my example- Type and URL is set to my test service which is running at http://192.168.20.35:8088/ in my internal network
-
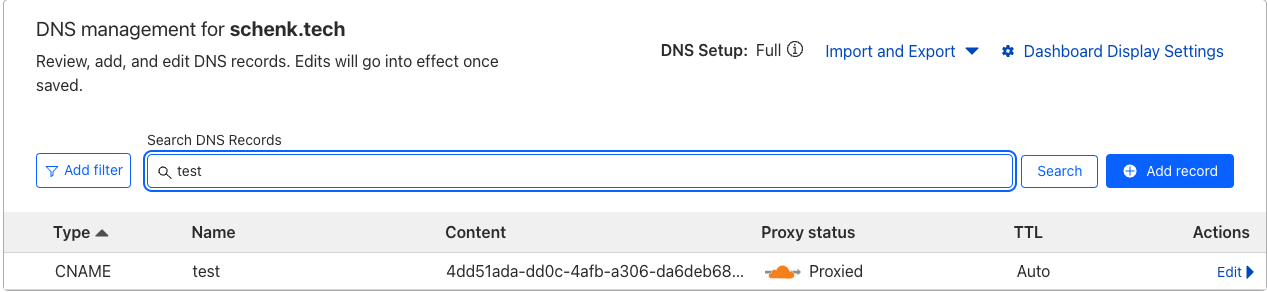
Click Save Tunnel
This will automatically create a DNS record that will proxy through the newly established cloudflare tunnel using the cloudflared service installed locally in the environment
Once the outbound connection is established with the Cloudflare global network, you will see a healthy connection to the internal service.
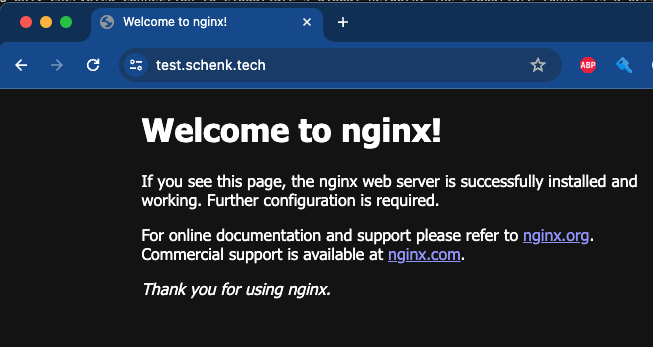
Now I can navigate to the new FQDN test.schenk.tech to test my service
Additional configuration can be done in the Cloudflare Dashboard under Access → Application configuration to restrict access, such as to a specific google workspace domain, or other identity provider.